Think of today’s higher education ecosystem as a digital vault that never sleeps. Every admission, exam, attendance update, and transcript entry passes through a student information system, quietly storing years of personal, academic, and behavioral data. This concentration of sensitive information has made higher education one of the most attractive targets for cybercriminals globally.
According to global cybersecurity studies, education institutions remain among the most frequently attacked sectors because of their large user base, distributed access, and valuable student data.
As a result, what was once considered a backend administrative platform has now become a frontline asset in the cybersecurity battlefield. A compromised student information system software can disrupt operations, expose personal data, and erode institutional trust within hours.
Artificial intelligence has transformed the way higher education institutions operate-but it has also reshaped the cyber threat landscape. While AI enables faster decision-making and automation within student information systems, cyber attackers are using the same technology to scale and refine their attacks.
AI-powered phishing campaigns now closely mimic institutional communication related to enrollment updates, academic records, and system notifications.
These messages are highly contextual, making them difficult for users to distinguish from legitimate alerts. Once credentials are compromised, attackers can quietly access the student information management system and observe data flows without immediate detection.
Additionally, automated attack tools analyze system behavior to identify weak access controls, misconfigured permissions, and unsecured integrations.
In a highly interconnected environment where student data flows across multiple modules, AI-driven attacks can adapt in real time-exploiting vulnerabilities faster than traditional defenses can respond.
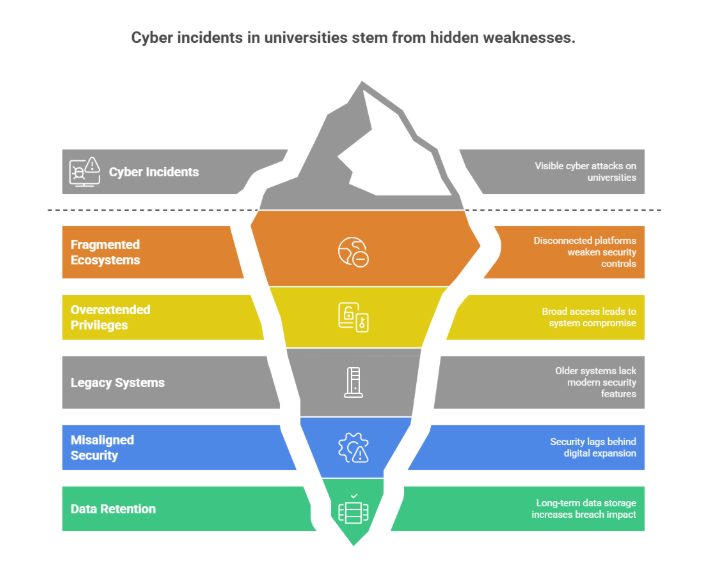
Cyber incidents in higher education rarely occur due to a single failure. Instead, they emerge from structural and operational weaknesses that attackers actively exploit.
In today’s threat environment, cybersecurity is no longer a purely technical function-it is a leadership responsibility. CIOs play a critical role in shaping how institutions perceive and prioritize the protection of student information systems.
Promoting a security-first campus culture begins with visibility. When leadership treats the student information management system as a mission-critical asset, security becomes part of everyday decision-making rather than an afterthought. Clear access policies, regular system audits, and consistent cybersecurity awareness across faculty and students help reduce human-led vulnerabilities.
Equally important is ensuring that security strategies evolve alongside institutional growth. As online student information systems expand, CIOs must align technology adoption with governance, monitoring, and accountability. The goal is not to restrict access, but to ensure that access is intentional, traceable, and protected throughout the student lifecycle.
Escaping modern cyber threats requires security that is built in, not bolted on. Protection must be embedded directly into the student information system software-and this is where Academia stands apart.
Rather than treating security as an add-on, Academia makes it a foundational part of the student data ecosystem, helping institutions protect sensitive information while maintaining compliance and operational continuity.
Cyber attackers have adapted quickly, learning how academic systems work and where institutions are most exposed. In this environment, safeguarding a student information system is no longer just an IT concern-it is a strategic imperative for institutional leadership.
By adopting a secure, cloud-ready, and resilient student information system software like Academia, institutions can protect student data, maintain operational continuity, and stay ahead of increasingly sophisticated cyber threats. Escaping the trap isn’t about reacting faster-it’s about being structurally secure from the start.

Experience Academia – Your partner in transforming campus operations, a trusted all-in-one ERP/SIS solution.
Get the latest insights, trends, and updates delivered straight to your inbox!